Vulnerability Diagram Ics Network
Free Printable Vulnerability Diagram Ics Network

Determine if the it and ics infrastructure is configured according to cyber security best practices.
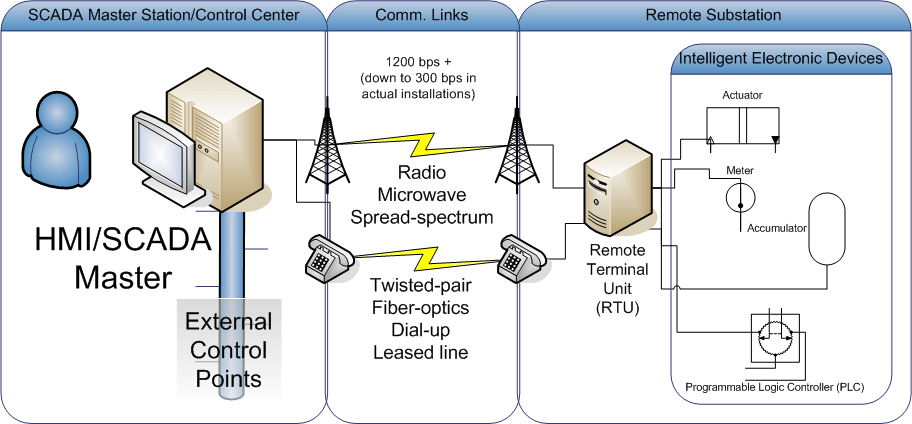
Vulnerability diagram ics network. With the proliferation of intelligent devices and networks it s simply not possible to effectively manage your iot and ics environment let alone protect it without this visibility. Ics components should not be accessible from the corporate information system and other external networks. Unify it scada and ics network security. Recommendations to strengthen the security level and how hardening can be applied.
According to our research an internal attacker already on the corporate information system would have been able to penetrate the industrial network in 82 percent of cases. Updates to ics risk management recommended practices and architectures. Ics components may be geographically scattered. So microsoft s warning great concerns.
Updates to security capabilities and tools for ics. At that point the attacker has a number of ways to perform malicious acts against ics components and the most. Additional alignment with other ics security standards and guidelines. On the industrial network internet access should be forbidden.
After exploiting vulnerabilities in the it infrastructure hackers can gain access to the industrial network. When a vulnerability scanner attempts to check for ssl issues the embedded http server can crash. The wannacry ransomware attack had disastrous effects and impacted businesses worldwide including industrial control system ics entities like automotive manufacturers rail service providers and some u s. Cyberx builds a network topology diagram using the purdue model showing how all devices are connected to each other as well as any connections to it networks.
Vulnerabilities inherent in the ics product 2. Updates to current activities in ics security. Known vulnerabilities in ics environments can be leveraged by threat actors to access the network and move laterally to execute targeted attacks. Updates to ics threats and vulnerabilities.
With the combination of ics scada smart scanning and passive network monitoring. Vulnerability patch and update management procedures enable organizations to secure off the shelf software hardware and firmware from known security threats. Process control is possible only from ics operator workstations within the industrial network. First the different sources of ics vulnerability information are summarized.
Identification of misconfigurations vulnerabilities and insufficient technical controls. Since the device is only designed to do one thing at a time this usually means the entire device reboots causing costly downtime and potentially unsafe. Then the common ics vulnerabilities are presented according to categories that describe a general problem observed in multiple ics security assessments. Skybox creates a logical model of your hybrid infrastructure security controls assets and vulnerabilities thanks to tight integrations with several ot security products.