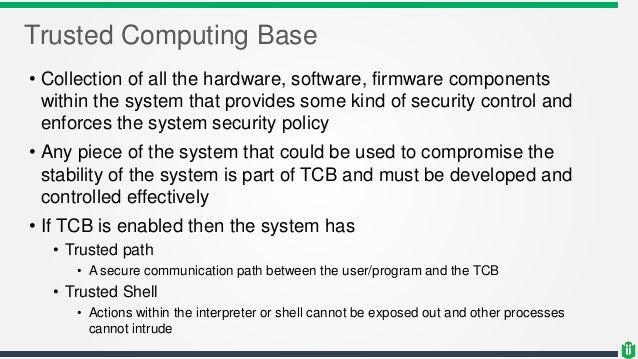
Trusted Computing Base Internal Network Diagram
Free Printable Trusted Computing Base Internal Network Diagram
Network diagram hosts the company s mission critical systems that are vital to the company s operations that also affect the overall financial situation.
Trusted computing base internal network diagram. Network diagram hosts the company s mission critical systems that are vital to the company s operations that also affect the overall financial situation. Network diagram hosts the company s mission critical systems without which the company s operations and financial. The company invested in the network and designed it to be fault tolerant and resilient from. Network diagram above is the global finance inc.
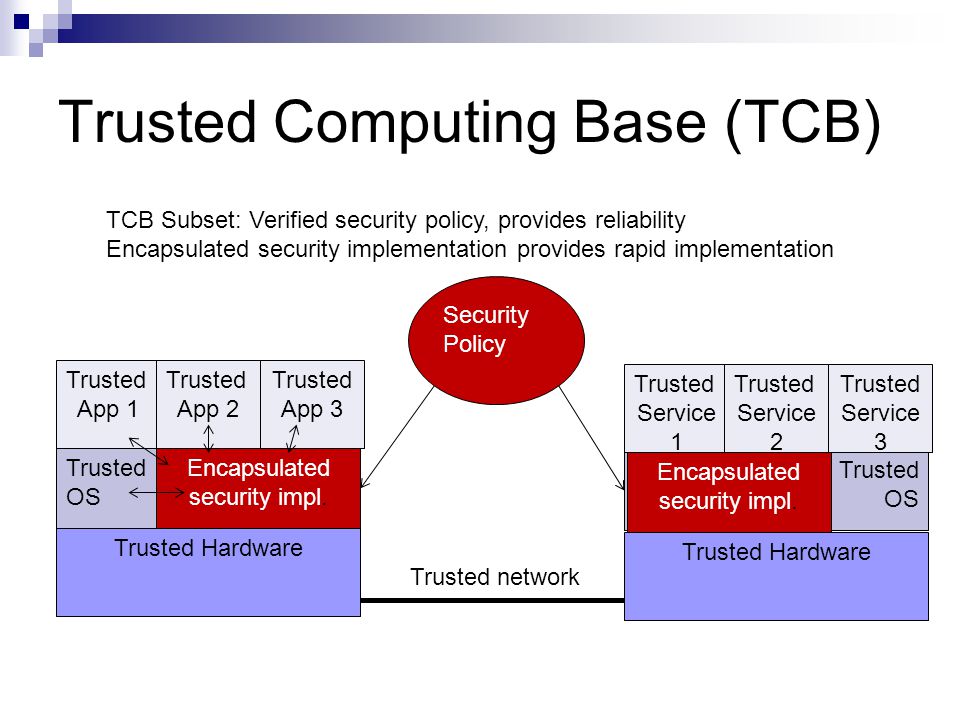
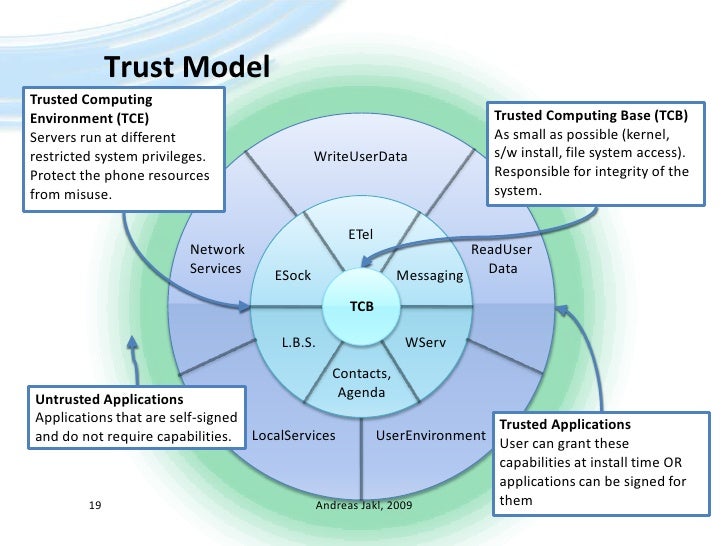
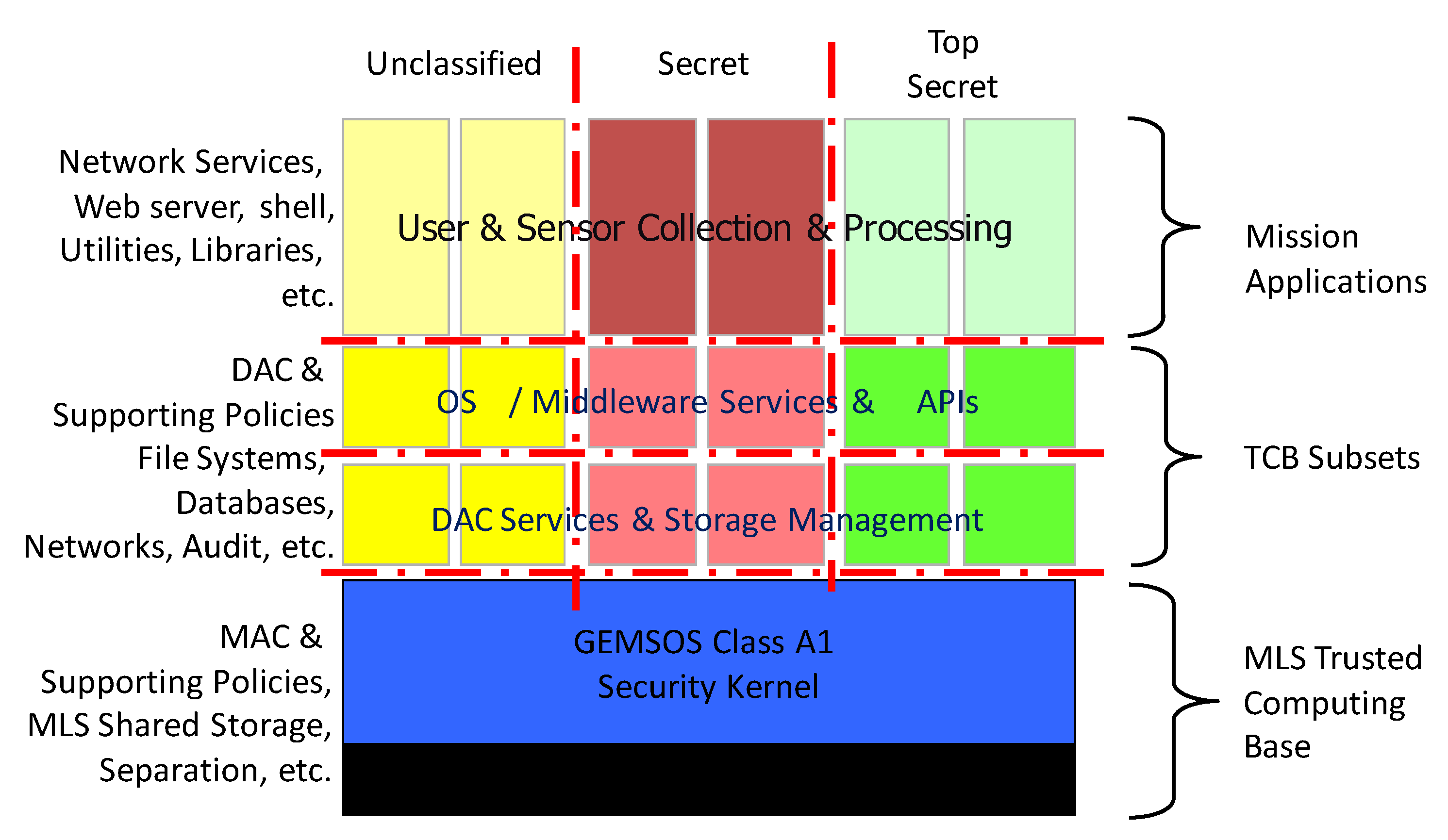
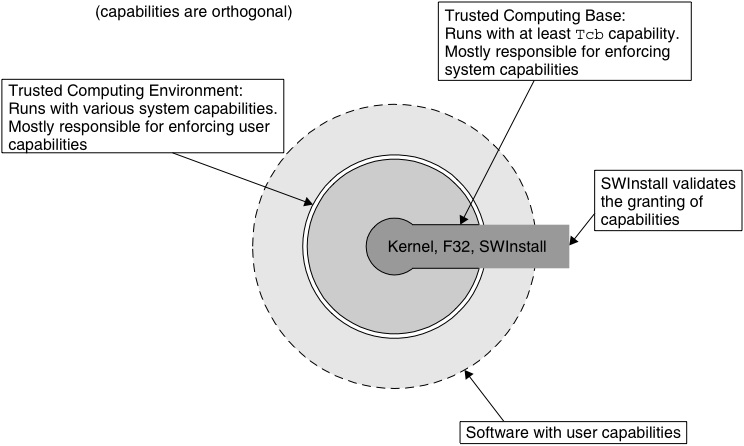
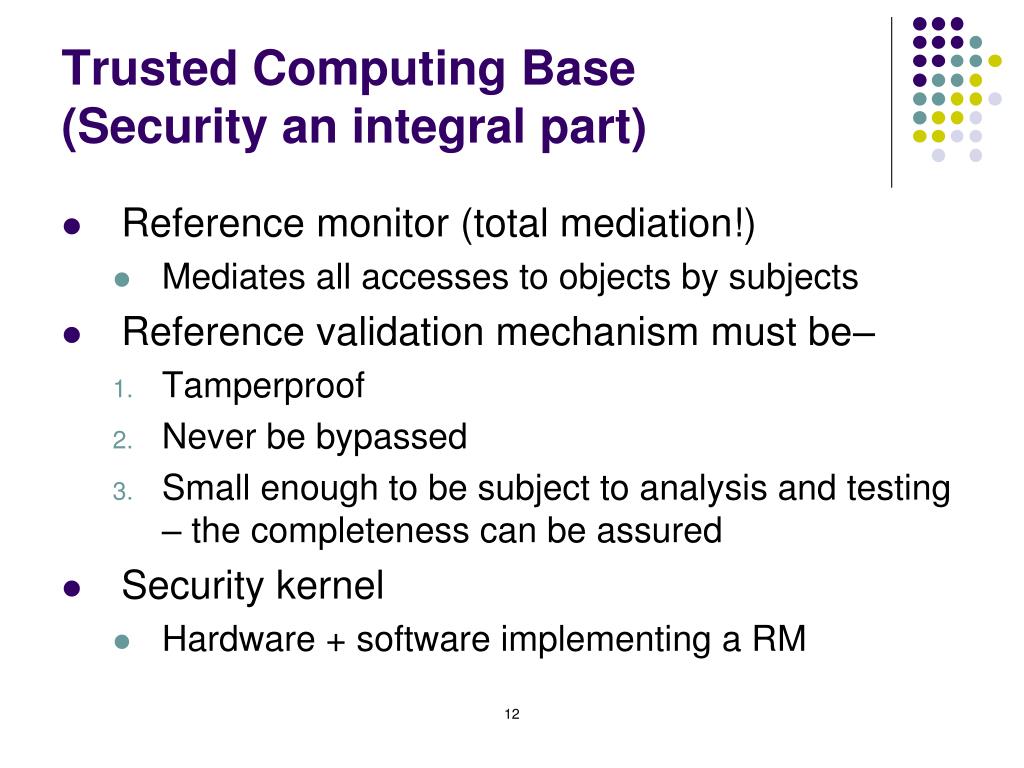
The trusted computing base tcb internal network within the global finance inc. The trusted computing base tcb of a computer system is the set of all hardware firmware and or software components that are critical to its security in the sense that bugs or vulnerabilities occurring inside the tcb might jeopardize the security properties of the entire system. The trusted computing base tcb internal network in the global finance inc. The oracle database and email systems are among the most intensively used application servers in the.
Gfi has grown rapidly this past year and acquired many network devices as displayed in the diagram. Trusted computing base tcb. The trusted computing base tcb internal network within the global finance inc. Network diagram hosts the company s mission critical systems that are vital to the company s operations that also affect the overall financial situation.
The oracle database and email systems are among the most intensively used application servers in the company. Trusted computing base tcb internal network within the global finance inc. Technical paper diagram global finance inc. Network diagram above is the global finance inc.
A hypothetical company gfi has grown rapidly this past year and implemented a number of network devices as displayed in the diagram. The trusted computing base tcb internal network within the global finance inc. The oracle database and email systems are among the most intensively used application servers in the company. Network diagram above is the global finance inc.
Network diagram hosts the company s mission critical systems that are vital to the company s operations that also affect the overall financial situation. Technical paper diagram global finance inc. The oracle database and email systems are among the most intensively used application servers in the company. This includes the operating system and its provided security.
A hypothetical company gfi has grown rapidly this past. The company invested in the network and designed it to be fault tolerant and resilient from any network failures.