Radius Auth Network Diagram
Free Printable Radius Auth Network Diagram
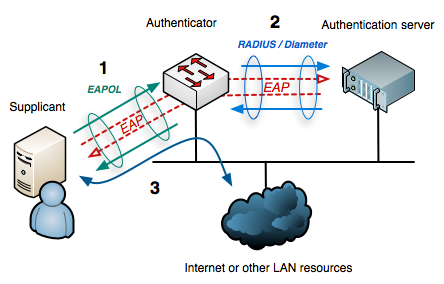
The user submits a username and a password which are encrypted by the radius server before being sent through the authentication process.
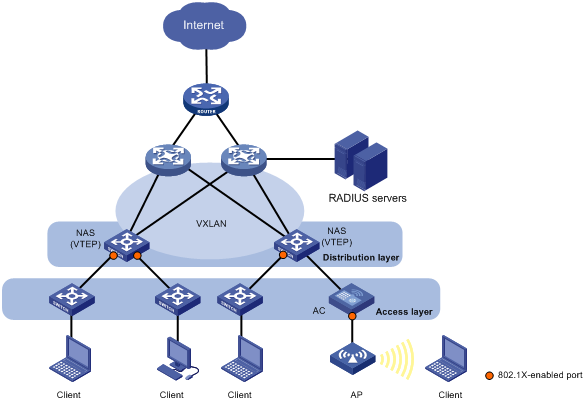
Radius auth network diagram. As a radius proxy nps forwards authentication and accounting messages to nps and other radius servers. You can use nps as a radius proxy to provide the routing of radius messages between radius clients also called network access servers and radius servers that perform user authentication authorization and accounting for the connection attempt. The radius server also collects a variety of information sent by the nas that can be used for accounting and for reporting on network activity. Diagram radius authentication visual cta installation.
Diagram radius authorization visual cta installation. If the psk matches the radius server s entry for the client s mac address the wireless client is authenticated and associated on the wireless network. Choose a radius profile for the ssid to use for mac authentication. The transaction listed in the network diagram above should take place.
Application or service send authentication request to duo security s authentication proxy. Select the wireless network that will have radius mac authentication enabled. Primary authentication using active directory or radius. The request may also include additional user information such as location or network address.
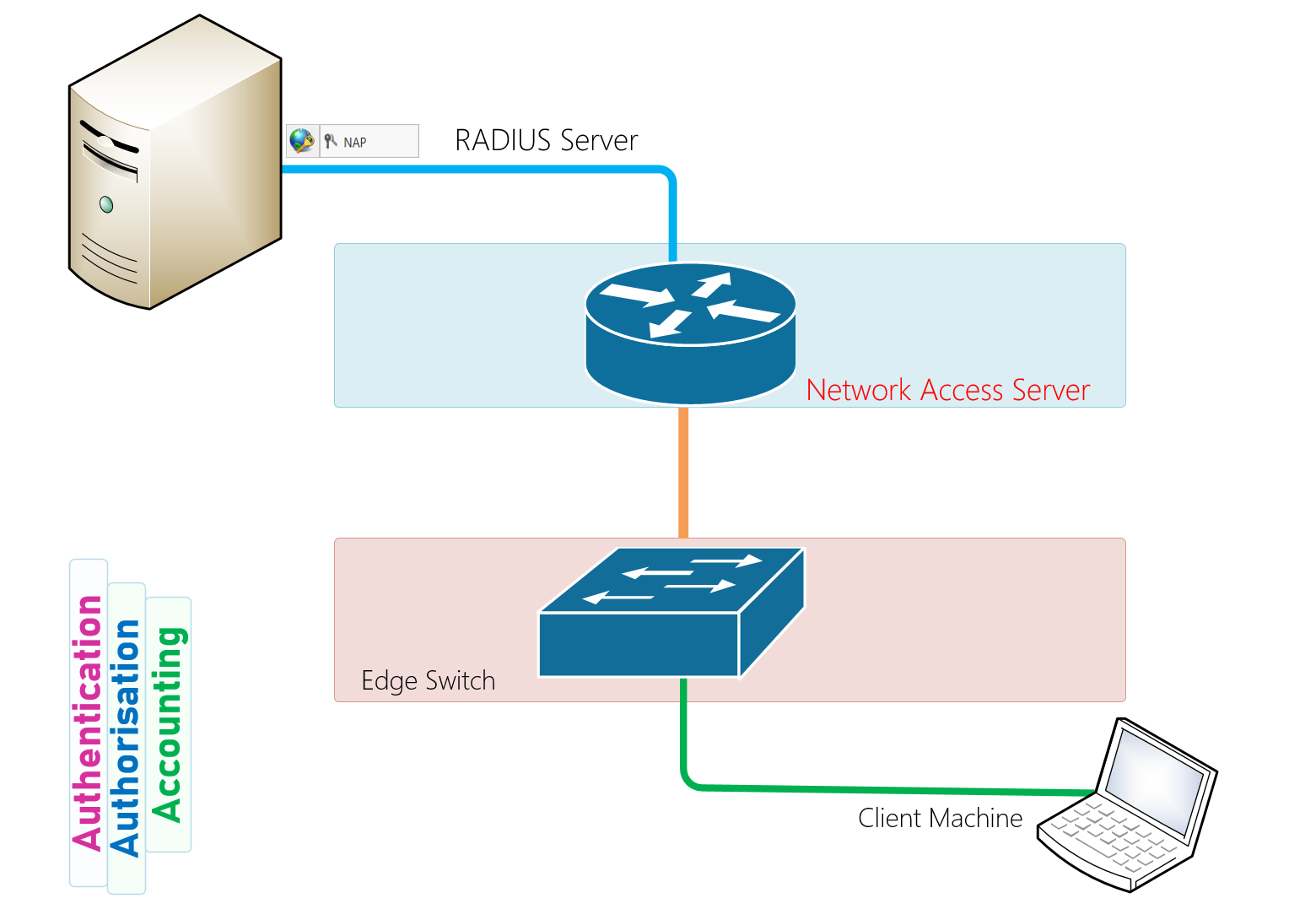
Remote authentication dial in user service radius is a networking protocol operating on port 1812 that provides centralized authentication authorization and accounting aaa or triple a management for users who connect and use a network service. The radius accounting standard rfc 2866 obsoletes rfc 2139. The radius specification rfc 2865 obsoletes rfc 2138. Navigate to settings wireless networks.
Verify with tcpdump on the unifi device whether the radius server is responding to the radius request. If the radius accept is returned move on in the steps below. In 1991 as an access server authentication and accounting protocol and later brought into. This configuration information is comprised of various authorizations.
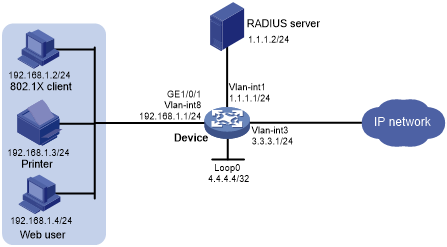
For more information on radius authentication and authorization see rfc 2865. Select the format to be passed as a username and password from the uap to the. The radius client sends information to designated radius servers when the user logs on and logs off. The radius server used for authentication can vary depending on the network.
Primary authentication initiated to application or service. The remote authentication dial in user service radius protocol was developed by livingston enterprises inc as an access server authentication and accounting protocol. If the server s request for authentication is accepted the radius server sends a series of configuration information to the network access server in order to grant the user access. Use the following command in an ssh session on a unifi device.
Configuring radius mac authentication. Duo authentication proxy connection established to duo security over tcp port 443.