Palo Alto Perimeter Network Diagram
Free Printable Palo Alto Perimeter Network Diagram

1 4 goto page.
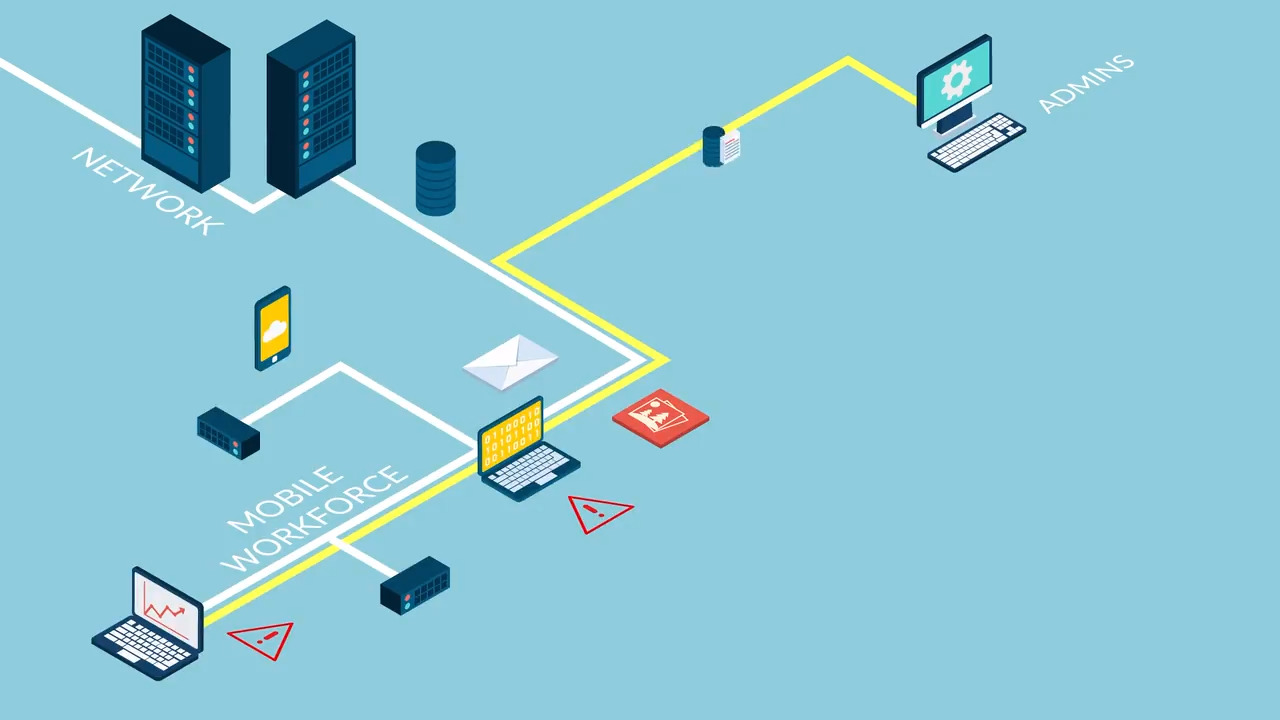
Palo alto perimeter network diagram. Created on 09 27 18 10 23 am last updated 03 11 20 15 52 pm. The core issue is the growing distance between the firewall that can provide security and the remote offices and users who need it. Establishing a logical perimeter a requiem for security policy. When inside the network security policy is well defined and based on.
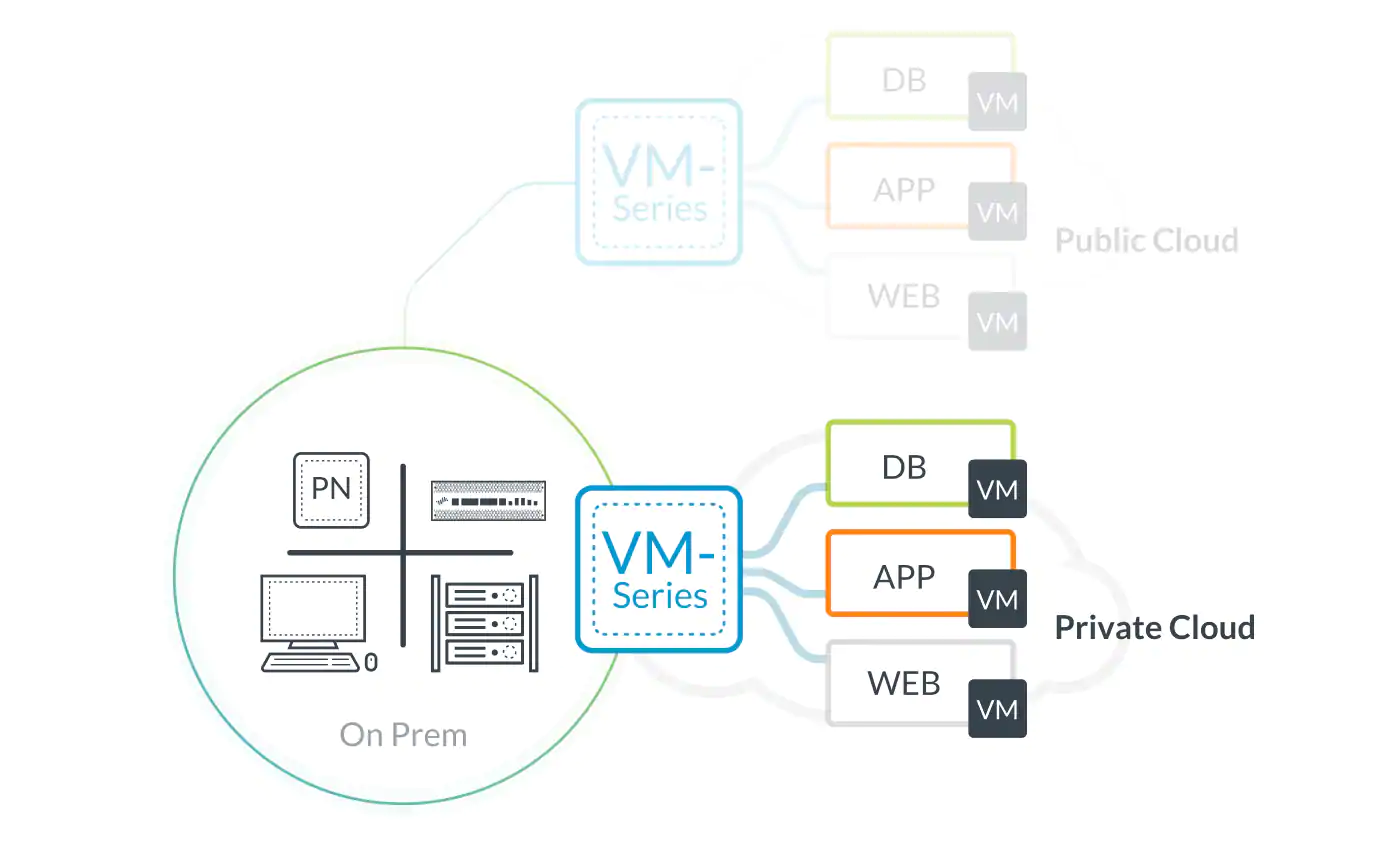
The palo alto firewall serves as. Let the diagram below be our working diagram. Every endpoint that participates in the globalprotect network receives configuration information from the portal including information about available gateways as well as any client certificates that may be required to connect to the globalprotect gateway s. Santa clara palo alto networks 3300 olcott st.
The latest palo alto networks visio stencils are attached to this article. Untrusta and the laboratory test subnet is 10 3 3 0 24 zone. Prisma access formerly globalprotect cloud service. Source user application application function url category and traffic destination.
The globalprotect portal provides the management functions for your globalprotect infrastructure. Technology brief the benefits of integration include. The server 10 3 3 5 needs to be reachable on the user side over port 80. Note that the user subnet is 10 1 1 0 24 zone.
The primary issue with a perimeter based network security strategy is that it relies on which assumption. There are several basic pieces of information useful for setting security policy irrespective of the function. For these reasons palo alto networks now provides a new option to protect networks and users around the world. Trust the routable private ip space is 10 2 2 0 24 zone.
When you choose palo alto networks to secure your network perimeter you get. Updated 11 march 2020 the latest palo alto networks visio stencils are attached to this article. Ca 95054 palo alto networks. What is a capability of the palo alto networks traps advanced endpoint protection product.
Palo alto networks certified network security administrator v1 0. Death by a thousand cuts the trends discussed above have led to an identity crisis of sorts for it teams and the corporate security policy in general. Given the cyber attack lifecycle diagram identify the stage in which the attacker can initiate malicious code against a targeted machine.