Oauth 2 0 Network Diagram
Free Printable Oauth 2 0 Network Diagram
The oauth 2 family of technologies has a number of business benefits enabling high performance apps with an extended reach.
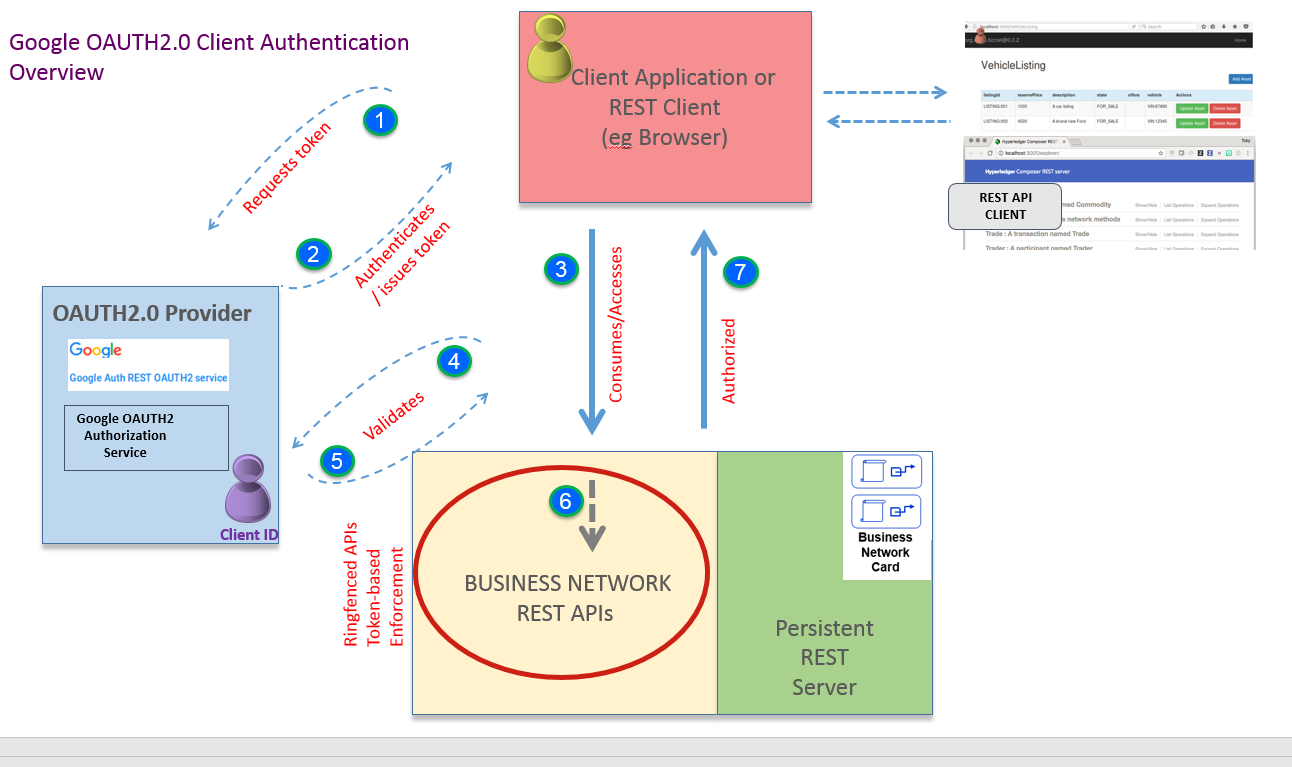
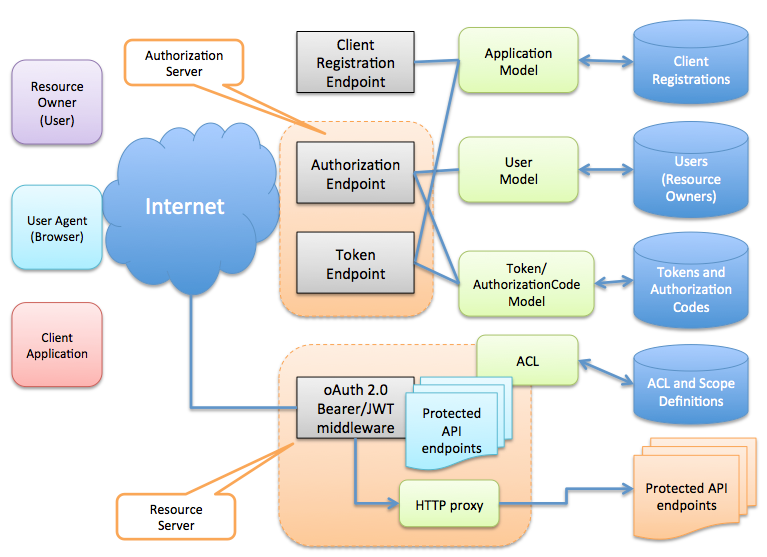
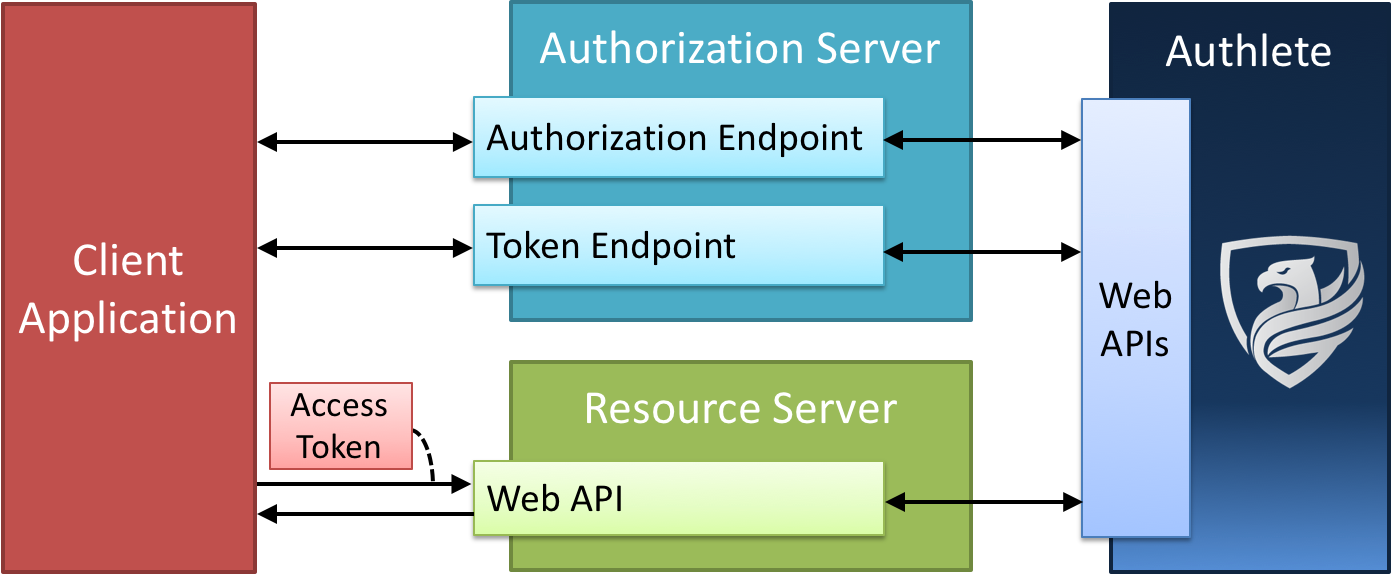
Oauth 2 0 network diagram. You get a package of sequence diagrams for all four oauth 2 0 flows. The authorization server which is the server that issues the access token. Step 2 next the client application will be provided with the client id and client password during registering the redirect uri uniform resource identifier. Oauth business benefits for companies.
For example a client implemented on a secure server. Oauth 2 0 flows are tricky. If you would like to grant access to your application data in a secure way then you want to use the oauth 2 0 protocol. The documentation on this page frequently refers back to these fields.
In this chapter we will discuss the architectural style of oauth 2 0. Confused by oauth 2 0 flows. Oauth 2 0 is a standard that apps use to provide client applications with access. The above diagram is from the identity server website which provides a very nice summary of why oauth 2 x and open id connect are the preferred security standards.
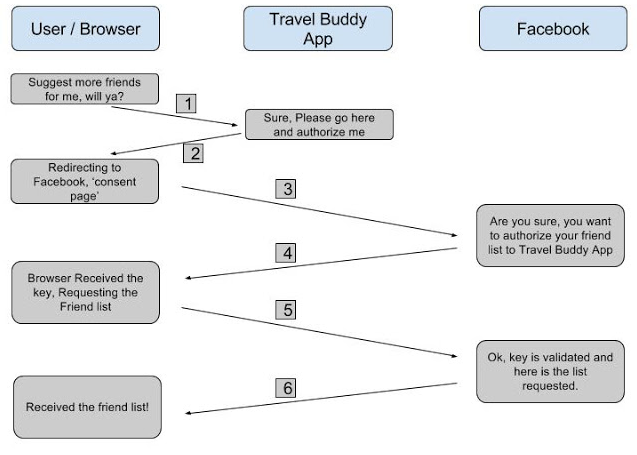
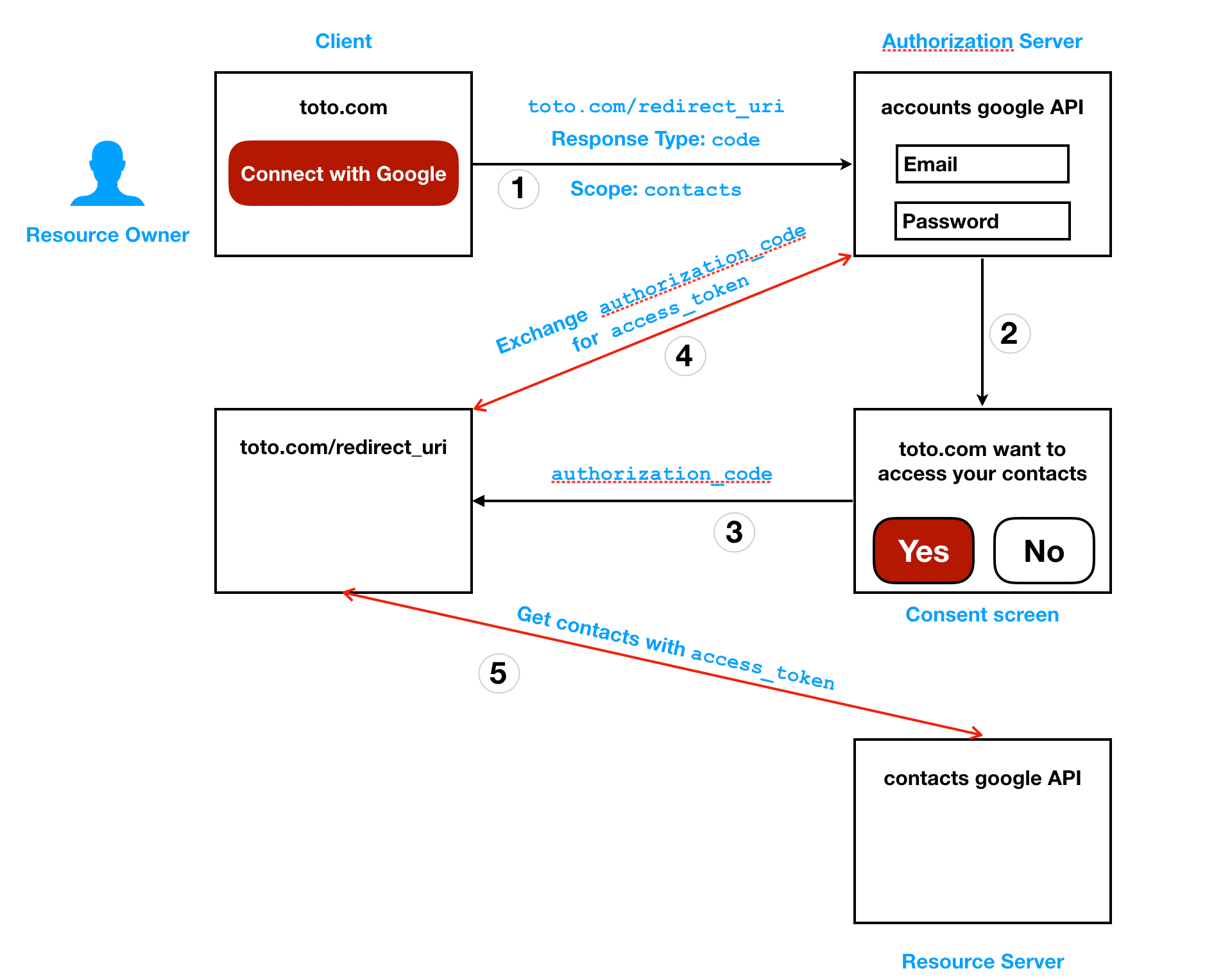
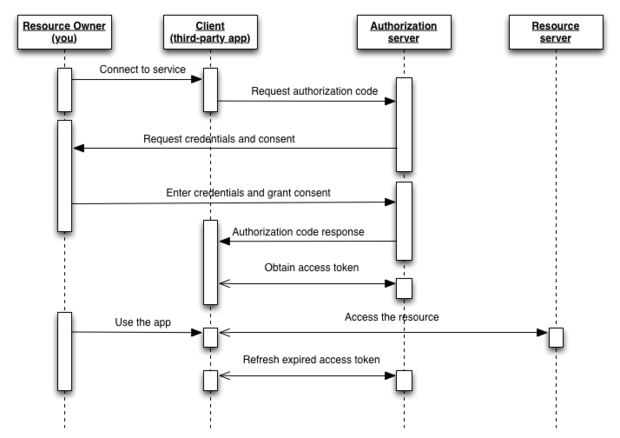
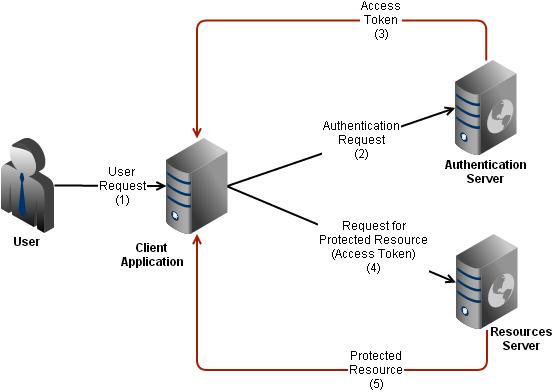
Consult the documentation of your oauth 2 provider to determine the appropriate values to put in each configurable field. A diagram says more than 1000 words. What do you get. Step 1 first the user accesses resources using the client application such as google facebook twitter etc.
Step 3 the user logs in using the. This is why i have created a set of sequence diagrams that visualize the various oauth flows defined in the standard. All of the oauth 2 0 fields that can be configured in halyard are detailed here.