Match Appropriate Security Devices With Network Diagram
Free Printable Match Appropriate Security Devices With Network Diagram

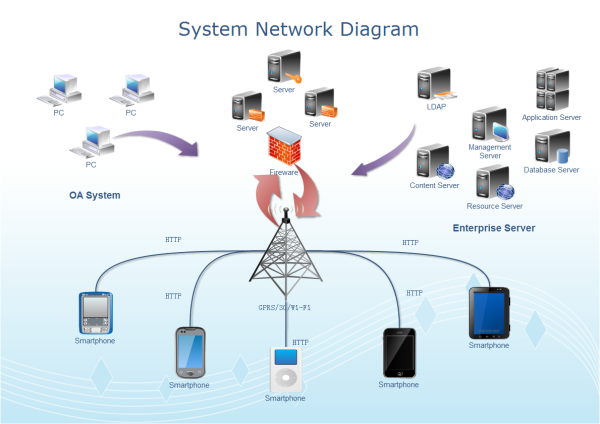
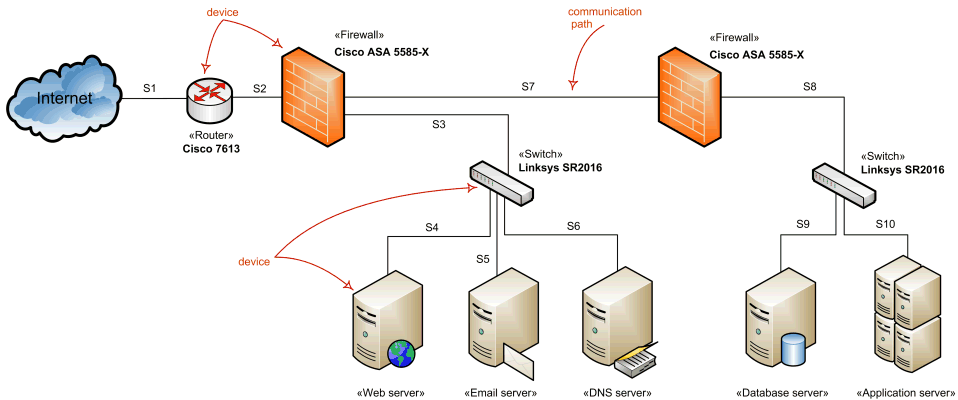
These devices include routers firewalls switches servers load balancers intrusion detection systems domain name systems and storage area networks.
Match appropriate security devices with network diagram. Gateways are generally more complex than switch or router. Network diagrams in project management are a visual representation of a project s schedule. This is the most important sub network to protect. A network diagram in project management is useful for planning and tracking the project from beginning to finish.
An experienced user spent 5 10 minutes creating. Network infrastructure devices are the components of a network that transport communications needed for data applications services and multi media. The samples you see on this page were created in conceptdraw diagram using the tools of network security diagrams solution for conceptdraw diagram software. Network security diagram access control and encryption.
Any potential risky activities should be avoided in this sub network. Different networking devices have different roles to play in a computer network. These symbols and examples can help you design accurate network diagrams quickly and you are able to save and share your own network diagrams with your team members. They show protection networks with firewalls and other network security devices.
Pre drawn network shapes are provided including 3d computers network devices and smart connectors. The broadcast packet travels to all devices on the same network segment asking for a response from the device with the target ip address. For example if the target device and the source device both have the network address 192 168 10 0 24 the source device safely assumes the target device is on the same network or network segment. Inline network devices this type of intrusion prevention strategy places a network device directly in the path of network communications with the capability to modify and block attack packets as they traverse the device s interfaces.
The above network diagram is an example of home network using subnets. Devices and computers here are used to store your most important data and perform your most important online activities. The design and structure of a network are usually shown and manipulated in a software created network topology diagram. These diagrams are essential for a few reasons but especially for how they can provide visual representations of both physical and logical layouts allowing administrators to see the connections between devices when.
Gateways are also called protocol converters and can operate at any network layer. It can work either at data link layer or at network layer. These devices are ideal targets for malicious cyber actors because most or all. Brouter it is also known as bridging router is a device which combines features of both bridge and router.